タスクのコスト管理などにタグをつけたい場合があるが、デフォルトではタグが付かないので設定を入れる必要がある。
※こんな感じ

やること
TerraformでECS(Fargate)環境を作成し、サービスとタスク定義にタグをつけ、それぞれ伝搬させてタスクにタグが伝搬されるか確認する。
実践!
1.下記を参考にECS環境を作成する。
amegaeru.hatenablog.jp
2.タグ伝搬設定
2-1.terraformに下記を追加
tags = {
"Name" = "example-task"
"Environment" = "Production"
}
tags = {
ServiceTagKey = "ServiceTagValue"
}
enable_ecs_managed_tags = true
propagate_tags = "TASK_DEFINITION"
2-2.適用
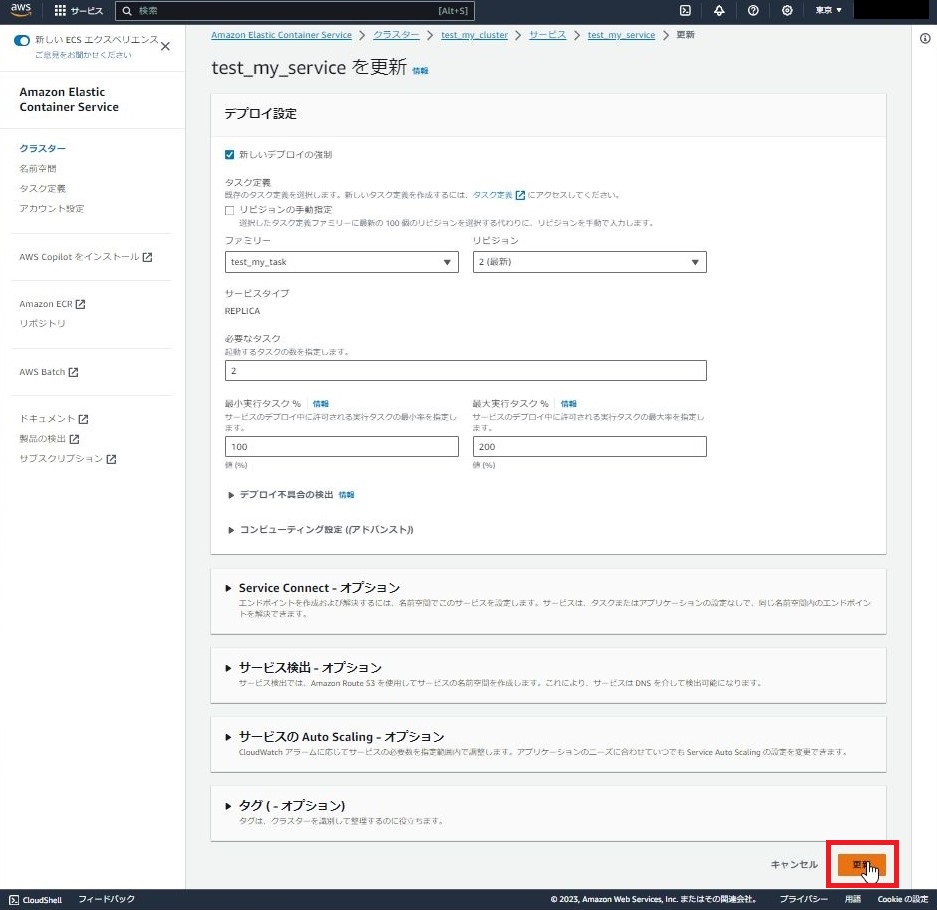
3.タスク更新
3-1.[ECS] - [Cluster] - [test_my_cluster] を押下

3-2.[test_my_service]を押下

3-3.[サービスを更新]を押下

3-4.[新しいデプロイを強制]にチェック

3-5.[更新]を押下
4.タグ確認
4-1.[タスク]タブを選択し、新たに作成されたタスクを選択

4-2.タスク定義のタグが伝搬されていることを確認

5.サービスからの伝搬に変更しタグ確認
5-1.Terraformコードを下記に変更
変更前)propagate_tags = "TASK_DEFINITION"
変更後)propagate_tags = "SERVICE"
5-2.適用
5-3.項番3を実施
5-4.項番4を実施し、サービスのタグが伝搬されていることを確認

6.設定確認
※GUIでは確認できないので、CLIで確認する
{
"services": [
{
"serviceArn": "arn:aws:ecs:ap-northeast-1:xxxxxxxxxxxx:service/test_my_cluster/test_my_service",
"serviceName": "test_my_service",
"clusterArn": "arn:aws:ecs:ap-northeast-1:xxxxxxxxxxxx:cluster/test_my_cluster",
"loadBalancers": [],
"serviceRegistries": [],
"status": "ACTIVE",
"desiredCount": 2,
"runningCount": 2,
"pendingCount": 0,
"launchType": "FARGATE",
"platformVersion": "LATEST",
"platformFamily": "Linux",
"taskDefinition": "arn:aws:ecs:ap-northeast-1:xxxxxxxxxxxx:task-definition/test_my_task:2",
"deploymentConfiguration": {
"deploymentCircuitBreaker": {
"enable": false,
"rollback": false
},
"maximumPercent": 200,
"minimumHealthyPercent": 100
},
"deployments": [
{
"id": "ecs-svc/4585009772463196880",
"status": "PRIMARY",
"taskDefinition": "arn:aws:ecs:ap-northeast-1:xxxxxxxxxxxx:task-definition/test_my_task:2",
"desiredCount": 2,
"pendingCount": 0,
"runningCount": 2,
"failedTasks": 0,
"createdAt": "2023-11-09T12:00:02.488000+00:00",
"updatedAt": "2023-11-09T12:03:12.223000+00:00",
"launchType": "FARGATE",
"platformVersion": "1.4.0",
"platformFamily": "Linux",
"networkConfiguration": {
"awsvpcConfiguration": {
"subnets": [
"subnet-07e57870668086b8d",
"subnet-07de7490b4eb4ac28"
],
"securityGroups": [
"sg-08189946c15738aae"
],
"assignPublicIp": "ENABLED"
}
},
"rolloutState": "COMPLETED",
"rolloutStateReason": "ECS deployment ecs-svc/4585009772463196880 completed."
}
],
"roleArn": "arn:aws:iam::xxxxxxxxxxxx:role/aws-service-role/ecs.amazonaws.com/AWSServiceRoleForECS",
"events": [
{
"id": "e474c982-7ec5-4adf-a819-41d19b261351",
"createdAt": "2023-11-09T12:03:12.231000+00:00",
"message": "(service test_my_service) has reached a steady state."
},
{
"id": "bdac6b90-0aee-4003-bf33-6526eb1e184a",
"createdAt": "2023-11-09T12:03:12.230000+00:00",
"message": "(service test_my_service) (deployment ecs-svc/4585009772463196880) deployment completed."
},
{
"id": "8a515cca-a02d-4414-8c98-713d12b684d0",
"createdAt": "2023-11-09T12:01:40.629000+00:00",
"message": "(service test_my_service) has stopped 2 running tasks: (task a1c1c765c65943fbb1f3e327cdb44c0e) (task 015212dd06bc4e369ef96837d2782b6a)."
},
{
"id": "b43b8358-4aaf-4f17-ab84-4b738a022cbf",
"createdAt": "2023-11-09T12:00:19.061000+00:00",
"message": "(service test_my_service) has started 2 tasks: (task 3ecf5e6e342544fcbeb983a00b2e6721) (task c2ecbb3d9dd94634a4a5ca62157ec298)."
},
{
"id": "f25855cb-445c-44ba-b770-873641ec1c4c",
"createdAt": "2023-11-09T11:27:52.929000+00:00",
"message": "(service test_my_service) has reached a steady state."
},
{
"id": "45228bd3-af38-48a3-9577-d20cc0d26926",
"createdAt": "2023-11-09T11:27:52.928000+00:00",
"message": "(service test_my_service) (deployment ecs-svc/1804178643143848991) deployment completed."
},
{
"id": "620b5c3e-94b4-403a-a6a3-520c1c2ccb80",
"createdAt": "2023-11-09T11:26:53.884000+00:00",
"message": "(service test_my_service) has stopped 2 running tasks: (task d73aa4a66d41462c9bda352c9d888512) (task bd727d24d56a4585b3123d19e31be1a4)."
},
{
"id": "67782c26-c27f-45d0-8a68-5d23e0227dcb",
"createdAt": "2023-11-09T11:25:40.600000+00:00",
"message": "(service test_my_service) has started 2 tasks: (task 015212dd06bc4e369ef96837d2782b6a) (task a1c1c765c65943fbb1f3e327cdb44c0e)."
},
{
"id": "99488bda-57ca-4088-ae2a-707db4a481ac",
"createdAt": "2023-11-09T11:23:36.513000+00:00",
"message": "(service test_my_service) has reached a steady state."
},
{
"id": "8407cdd3-1adc-4712-91c1-ad9a58aec04c",
"createdAt": "2023-11-09T11:23:36.512000+00:00",
"message": "(service test_my_service) (deployment ecs-svc/2246503820580644060) deployment completed."
},
{
"id": "6b9a85ab-5c09-4167-9783-e6cd1093dbc9",
"createdAt": "2023-11-09T11:22:13.933000+00:00",
"message": "(service test_my_service) has stopped 2 running tasks: (task ef71f61e777945179bde60c810cb356c) (task 9234724d9df34a878960a9edad786b18)."
},
{
"id": "fade1152-e3de-41a6-a3ac-dfb8452cf32a",
"createdAt": "2023-11-09T11:21:03.337000+00:00",
"message": "(service test_my_service) has started 2 tasks: (task bd727d24d56a4585b3123d19e31be1a4) (task d73aa4a66d41462c9bda352c9d888512)."
},
{
"id": "36fa0e83-48f1-42e4-850e-8aa3c59ddf53",
"createdAt": "2023-11-09T11:20:41.411000+00:00",
"message": "(service test_my_service) has started 2 tasks: (task 9234724d9df34a878960a9edad786b18) (task ef71f61e777945179bde60c810cb356c)."
},
{
"id": "4bd549c4-bdea-4ea2-bf11-c87f769b1f7a",
"createdAt": "2023-11-09T11:12:56.255000+00:00",
"message": "(service test_my_service) has reached a steady state."
},
{
"id": "4f0d0ba5-6b17-4759-9c1a-c7cdfcf98c87",
"createdAt": "2023-11-09T11:12:56.254000+00:00",
"message": "(service test_my_service) (deployment ecs-svc/2241376552719585905) deployment completed."
},
{
"id": "e15f792d-3f1c-4249-a2ca-464d54021366",
"createdAt": "2023-11-09T11:12:28.285000+00:00",
"message": "(service test_my_service) has started 2 tasks: (task 6734ffc09f0f47b883e04df2a511f189) (task c59eae0b798b4c2d8e61b47cd928b9f9)."
}
],
"createdAt": "2023-11-09T11:12:22.106000+00:00",
"placementConstraints": [],
"placementStrategy": [],
"networkConfiguration": {
"awsvpcConfiguration": {
"subnets": [
"subnet-07e57870668086b8d",
"subnet-07de7490b4eb4ac28"
],
"securityGroups": [
"sg-08189946c15738aae"
],
"assignPublicIp": "ENABLED"
}
},
"schedulingStrategy": "REPLICA",
"deploymentController": {
"type": "ECS"
},
"createdBy": "arn:aws:iam::xxxxxxxxxxxx:user/vaultuser",
"enableECSManagedTags": true,
"propagateTags": "SERVICE",
"enableExecuteCommand": false
}
],
"failures": []
}
感想
ECS奥が深いねぇ(´Д`)